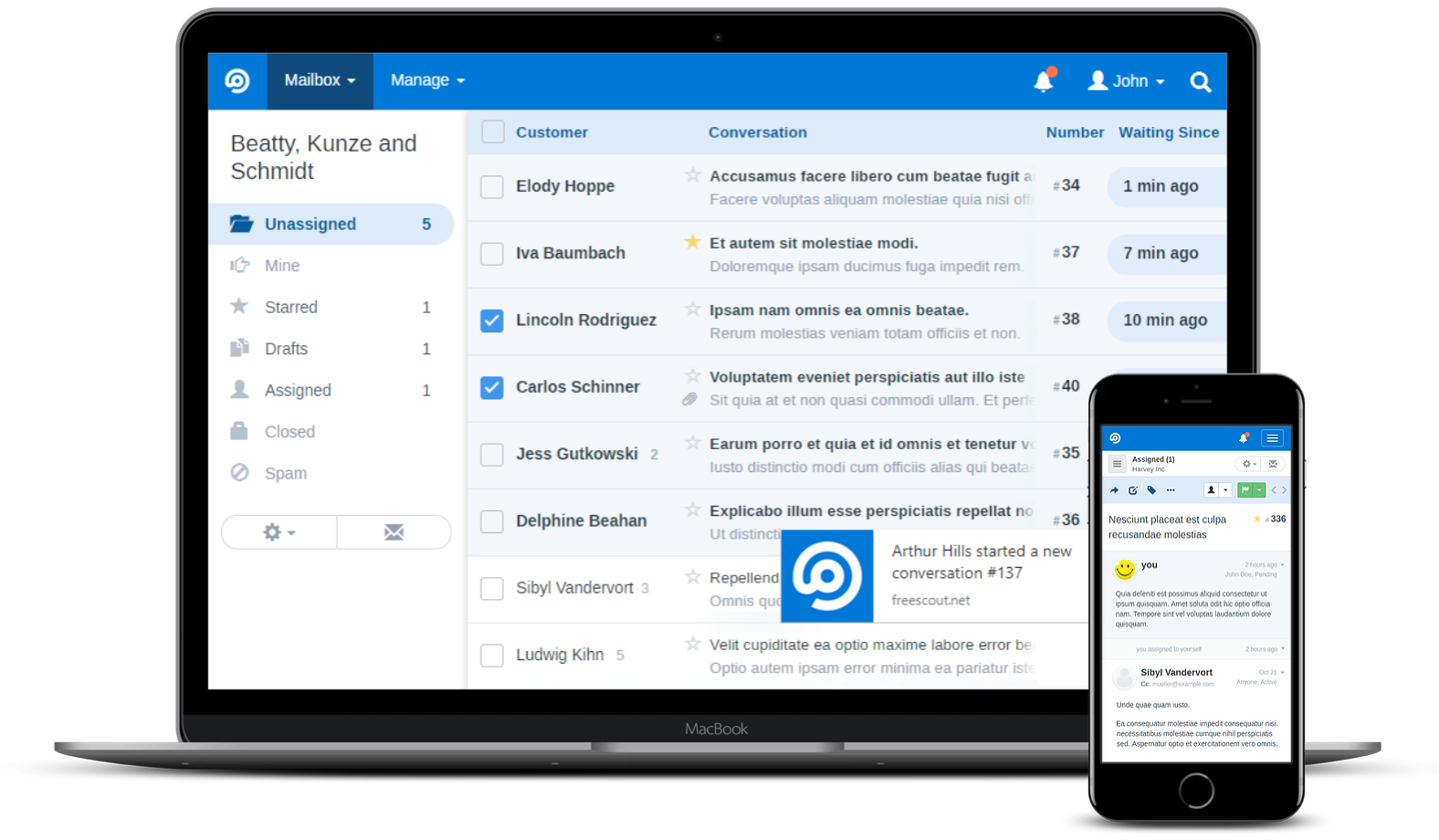
HelpScout raised its prices again. Our use of the service has not changed over the years, yet somehow we’re now paying over $100/month for a glorified mailbox. Enough is enough.
The new setup? An $8 Digital Ocean VPS + $2 for daily backups and FreeScout. This little server holds our archive of over 40.000 conversations and has ample space for years to come.
While FreeScout is free, I did purchase a ton of their plug-ins to tailor it to our needs. Those come at a one-time fee – no monthly charges. I also created some plug-ins of our own, see below.
Setup FreeScout
I used Ubuntu 24.04 LTS and followed the manual setup instructions with a few small tweaks:
- PHP 8.4 (instead of the 8.0 suggested). I later downgraded to PHP 8.3 due to a bug in PHP 8.4.
- 200M upload limit (instead of the 20M default).
Migrating data
Joost’s blog suggested using help-desk-migration.com. While their trial migration worked well, their fee of USD ~$2000 didn’t make sense to me.
I asked ChatGPT to create me a script to handle the migration. Which it did. All conversations, including attachments, were successfully copied to our new FreeScout install.
In case you need this yourself, this was my prompt:
I want to copy all my data from HelpScout to FreeScout. This should be an intelligent copy. Specifically, it should not copy data that was already copied previously. The code, written in PHP, should not have dependencies. It should be short and concise and readable code.
I haven’t double-checked ChatGPT’s code, hence I’m not posting here. It worked for me, but may very well burn your house down. By the time you read this, ChatGPT has probably evolved and will create you something even better than it did me.
Tweaks and Plug-ins.
There were a couple of changes I needed to make manually.
Custom Apps
I was missing the ability to pull in information from our CRM. In HelpScout I used their Legacy Custom App feature to do this. Fortunately it was not too difficult to create a simple FreeScout plugin that functions similarly: CustomApp.
Fast Search
FreeScout’s default search is very slow and their FasterSearch plug-in requires me to upload data to a 3rd-party – a no-go. I created a small plug-in that leverages MariaDB’s full-text indexes to perform the search. This turned out to be significantly faster: FastSearch.
Redis
After running into a GitHub issue regarding Redis, I decided to create a Redis module as well: RedisDriver.
AI Assistant
Sometimes you get assigned a conversation with a lot of history. To avoid having to go through a dozen e-mails of troubleshooting history, I’ve created an AI Assistant module that summarizes long running tickets.
E-mail Fetching
I’m not a fan of polling the mail server once a minute. It introduces an unnecessary delay in the interaction with the customer. Ideally we would setup Postfix to submit the raw e-mail to a FreeScout API endpoint in real-time. This is how most other ticketing systems let you do it.
Unfortunately FreeScout’s message parsing is tightly integrated with its IMAP/POP3 fetching. This makes it difficult to create a second path for raw e-mails without duplicating a lot of code (and then maintaining it..)
As a work-around, I’m having CRON fetch e-mails more frequently:
* * * * * www-data php /var/www/html/artisan schedule:run >> /dev/null 2>&1
* * * * * www-data ( sleep 10 ; php /var/www/html/artisan freescout:fetch-emails ) >> /dev/null 2>&1
* * * * * www-data ( sleep 20 ; php /var/www/html/artisan freescout:fetch-emails ) >> /dev/null 2>&1
* * * * * www-data ( sleep 30 ; php /var/www/html/artisan freescout:fetch-emails ) >> /dev/null 2>&1
* * * * * www-data ( sleep 40 ; php /var/www/html/artisan freescout:fetch-emails ) >> /dev/null 2>&1
* * * * * www-data ( sleep 50 ; php /var/www/html/artisan freescout:fetch-emails ) >> /dev/null 2>&1
I’ll probably change this to every 5 seconds if the IMAP server allows.
CSS
Because FreeScout is modeled after an older version of HelpScout, the default appearance is a bit dated. I added the following CSS to their Customization plug-in to improve this a little bit:
.sidebar-buttons {
padding-left: 5px;
padding-right: 5px;
}
.sidebar-buttons .btn-group a.btn {
border-radius: 5px 0 0 5px;
}
.sidebar-buttons > a.btn {
border-radius: 0 5px 5px 0;
}
.dropdown-menu {
border-radius: 5px;
}
.sidebar-2col {
padding-right: 0;
}
.content-2col {
border-left: 1px solid #d6dde3;
-webkit-box-shadow: none;
}
.sidebar-menu > li > a {
border-radius: 0;
}
.sidebar-menu > li {
border-radius: 0;
}
.conv-active .conv-date a {
background-color: inherit;
}
.btn {
border-radius: 5px;
}
.panel-group .panel {
border-radius: 5px;
}
Bonus Benefits
In addition to replacing HelpScout, FreeScout also offers a few extras that we didn’t have when using HelpScout:
- Telegram integration – customers can correspond with us through Telegram.
- In-line translations. The translations plug-in is a real time saver. It remembers the translations so you don’t have to fiddle with the browser’s translation feature every-time you re-open a ticket in a foreign language. Frankly, this feature alone, makes it worth switching to FreeScout.
0 comments